First Impressions
You can download a trial version of G Data Internet Security 2011 easily enough and they don't require any personal information. What is required though is a bit of patience. G Data Internet Security 2011 is large, huge in fact. The download comes in near 300 MB and is clearly the largest of any solution I've reviewed thus far.
G Data sports a pretty basic installation wizard but does allow for some customization. You can choose to install the full version or a fully functional 30 day trial version. By default the Antivirus, Antispam and Firewall modules are installed. Additional modules (disabled by default) include the Shredder and Parental controls. This review has been done using the default configuration.
G-Data Internet Security 2011
Moving through the installation you'll find G Data is set to check for updates hourly and to perform a computer scan weekly. A single reboot is required before G Data is set to protect your system. The problems for me began after the reboot.
G Data does end the Windows Firewall service but does not end the Windows Defender service. The latter you will need to do yourself, assistance can be found here. G Data attempted an initial update but requires registration before an update can be performed. The registration form is simple enough allowing for a fast or full login. I was not thrilled that a checkbox is selected by default which appears to opt you in to receive junk mail from any number of sources.
G-Data Internet Security 2011
Unfortunately, once I submitted the form I was met with a message noting the product had already been registered and has expired or would expire soon. If you cannot register you cannot receive updates. It's as simple as that. Obviously this is a problem.
G-Data Internet Security 2011
I keep my test system ready for complete recovery and thought there may be something wrong on my end that caused this registration issue. I performed a complete system recovery and after applying the current Windows updates moved through downloading and installing G Data Internet Security 2011 again. I encountered the same problem. My next course of action was to visit the G Data site and review the FAQ (Frequently Asked Questions) area of their support site. Further disappointment was encountered here as a search turned up nothing helpful and the list of applications to narrow a search on does not even include the latest products, nor did it include any version for the past several years. I was confused.
G-Data Internet Security 2011
Having no success on the support site I decided to contact G Data support via email. After several days I received a response which basically said they had no record of my email as a registered user and could I access the update options and let them know the registered name. Of course there is no name because I haven't been able to register. I shared this information, along with screenshots, in a response. This last message has yet to see a reply.
G Data does indeed check for an update every hour as scheduled and subsequently failed each hour as well.
Sure, there is a chance they placed a faulty trial version on their site and maybe their registration process was broken too, and maybe they were updating their FAQ's when I was looking for help. All of these may be forgivable for a startup or beta application but for one that has been in business for 25 years?
Needless to say, my initial impression is not very good.
Ease of Use and Configuration
Working with G Data Internet Security 2011 is not too difficult. The interfaces presented are largely minimalist in design and the options are few and pretty straightforward. The main interface provides all the pertinent stats around when a scan was last performed, the last time an update was done and whether or not the various protection modules (firewall, virus monitoring etc) are enabled. The More functions link within the Virus check section allows easy access to different types of scans as well as a link to access the quarantine.
G-Data Internet Security 2011
You will find options associated with virus scanning, update processing and Internet and Email protection. The Virus checkoptions host the typical settings such as what the default clean action should be and how to treat infected archive files. There is also the option to have G Data pause scanning activities if the system load is high. G Data utilizes two scanning engines, both engines are enabled by default which is the recommended and default configuration. You do have the option to only use one engine if you like. I imagine performance concerns may be the only good reason to choose single engine scanning.
G-Data Internet Security 2011
The Monitor tab of the virus options is where you will find advanced settings. These settings are largely in the form of turning on or off features via a checkbox and include items like heuristic scanning, checking system areas during start and, among others, checking for spyware.
Within the Update section you'll find options for scheduling updates or forcing a manual program update. In the image below you'll notice the UAC icon present next to the update link. This means elevated privileges are required to perform an update. This isn't a good thing since it requires administrative access of the user trying to perform the function. If the user doesn't have administrative access the update cannot be performed. Unfortunately a UAC prompt is issued for most major actions, including a system scan. I'll discuss this more in the Antivirus section.
G-Data Internet Security 2011
The firewall configuration is non-intimidating and allows for management of the usual settings. Here you change how a network is defined (trusted or not) and define rules to allow and deny applications and ports. There is also a convenient space for you to identify exceptions in the form of a whitelist of sites that should be allowed. Unfortunately even this function forces a UAC prompt.
G-Data Internet Security 2011
Accessing the more advanced settings within the firewall requires you to select the Edit link from the Firewall settings status pane. This isn't exactly intuitive but is at least found on the main setting interface. G Data is configured to run in autopilot mode by default which restricts your access to the advanced features unless you choose the Custom Security (for professionals) option. With this option selected you can set options around the type of attacks to detect, edit settings related to creating rules, how the system should respond to unknown server applications and whether or not you should be notified when connecting to new networks if you are unprotected.
G-Data Internet Security 2011
While G Data Internet Security 2011 is not difficult to use or configure, the number of actions that require elevated privileges is surprising. No other security application reviewed, with the exception of the 64-bit version of BullGuard Internet Security 9.0, presented this barrier to security.
Firewall
The G Data firewall is as unobtrusive as any I've tested thus far. I've been testing for more than a week and not one prompt has been issued (aside from forced scans) nor have any applications been blocked. This speaks pretty well of the default auto-pilot configuration. The Firewall settings are minimal but sufficient and allow you to define rules for allowing or blocking ports and applications. This will satisfy most novice users but may fall short of what a user experienced in managing security setting would expect.
G-Data Internet Security 2011
In my testing of the firewall I like to perform an intrusive scan from a couple of different sources, namely Nessus and Nmap. When my test system was scanned G Data immediately identified that a scan was underway and displayed a notification along with a link to some information about the system performing the scan. The latter is a nice feature to help identify the attacker right away and is something a bit unique to G Data. This information may be available in most other suites but you will likely have to look into the security logs to find the offending machine.
G-Data Internet Security 2011
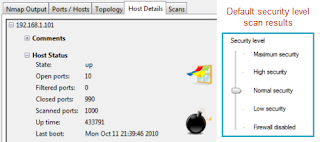
Despite G Data doing a fine job of identifying the scan, the firewall did not perform exceptionally well at limiting the amount of information the scan was able to collect. Nmap identified the system as being vulnerable based on more than 9 ports found to be open. The netbios information derived was also more than I was comfortable with. I rescanned the system after changing the firewall settings from Normal Security to High Security and the results improved by significantly reducing the number of open ports.
G-Data Internet Security 2011
There is a default setting within the firewall that will notify you if you are connecting to an unprotected network. Regardless of which network I connected to I could not get this prompt to display. I consider this prompt essential to good security especially considering the poor scan results with the default configuration. If the prompt were to display, you would then be reminded to adjust the security level manually which is far better than simply having to remember to do it.
G-Data Internet Security 2011
The firewall does a nice job of not getting in your way which is a fine characteristic. Unfortunately the default protection could be better. At the very least some minor changes could be made to the interface that would place the user in a position to change the security level in certain instances, such as connecting to a new or unidentified network.
Antivirus and Antispyware features
When it comes to antivirus and antispyware detection G Data Internet Security 2011 shines. I threw several infected files at the test system and each were identified quickly and without issue. The default action upon detecting a threat is to disinfect the file, if possible, or quarantine, if disinfection is not possible. This can be changed easily within the settings, if your preference is to be prompted for the action to take.
G-Data Internet Security 2011
As mentioned previously, the real downside with the antivirus and antispyware feature is the fact that you have to answer a UAC prompt whenever a scan is initialized. This is true of a scheduled scan as well. This is very unfortunate since it means a scan could never be performed if the user initiating it does not have administrative access. Ultimately this implementation results in a less secure system regardless of how good the detection engines are. Thankfully the real-time protection does not appear to suffer and performs as one might hope.
Presumably the detection of threats in the browser also works well however, I was not able to force a prompt to display. This can be difficult to test as many malicious sites are closed shortly after being detected. It may also have to do with the difficulties I encountered with registration issues which kept the application from updating beyond the April 2010 definitions the trial version was equipped with.
Thankfully you don't need to rely on my testing alone. The team behind av-comparitives.org awarded G Data the Advanced+ (best) rating in their testing of Internet Security 2011.
The antivirus setting are easy to adjust and just as easy to understand. They also have proven to be very effective. Unfortunately the nagging UAC issue keeps it from being as effective as it could be.















0 Comments:
Post a Comment